first published 2 Feb 2024
Hi! This is one of my articles you can read, where I delve into a cheap Chinese flash drive with more attention than it probably deserves.
Until I finish the website to the point of being comfortable to browse and read, I hope you enjoy a taste of things to come :)
(note: I use the term “flash drive” and “pendrive” interchangeably as I write. Cultural considerations – where I’m from we only call them “pendrive”; sorry if it irks you.)
Ahhhh, flash drives. How would the world look without them?
Admittedly, nowadays sneakernet seems to be pushed out by cloud and Internet-based services more than ever – raise your hand if you ever transferred files between two of your devices by using Google Drive or Facebook Messenger, like me – but pendrives still find a lot of usecases. And sneakernet is just one of many - printing, live CDs, sharing pics on your TV, transferring files onto retro PCs – they’re still great to have handy and have gotten cheap enough that when one inevitably gets lost or its USB connector gets torn off, you can get one almost anywhere and for chump change.
I am fortunate enough to remember and have used various neat data transfer methods – apart from the usual suspects, I once wasted a whole CD-RW spindle because I didn’t know jack about how to use them. IrDA was fantastic and I remember a time where me and my friends would pool some moolah together to buy a game from the back cover of a magazine, then distribute it between ourselves using Infrared. It was amazing, if a little frustrating when the break had ended before the transfer was complete. Tough luck. Even worse if your phone had a different screen resolution than the game .jar was designed for (who remembers that nuisance?). Continuing, early Bluetooth, Sony Memory Sticks and hateful M2 cards, P2P networks, eMule, Bearshare - oh, how I miss those two; LAN workgroup-folder sharing-kind-of-thing that my uncle set up between our houses (it was absolutely mindblowing for me as a greenhorn PC user) – heck, even MP3 players were used in a pinch. But all those paled in comparison to the great flash drive once it had become “normal” for Joe, Jane and little Jim Schmoe to own one. In hindsight, one could be struck in awe of how quickly they proliferated and turned out to be the primary non-network means of sharing data, as well as how their size had increased in such a rapid pace – my very first pendrive back in 2009 or so had a whopping 1 gig of size, and it was the bee’s knees. It could even play MP3s. Yes, as above, my first “pendrive” really was an MP3 player that I used to share game trainers and other “cool” stuff with kids in primary school. Good times!
One time around 2018 I received a 64GB flash drive, the subject of this article, as part of a first place prize in an IT/English school contest. That event was quite interesting for other reasons concerning computers and tech – but perhaps these will be mentioned in another post. Funnily enough, I also won an incredibly cheap powerbank that I never got to use, as it didn’t work at all – I got it out of the box, it would charge forever, and it would shut down immediately after disconnecting the charger. It had a flashlight, though, and that worked just fine! The prize flash drive was quickly confined to the drawer jail and was promptly forgotten as I simply did not need another pendrive – I already had a handful in different sizes. Recently though, I unearthed the little demon and it just so happened that I needed an empty pendrive handy for a Debian bootable USB for some testing.
In truth, however, all this time I knew that I wouldn’t use it for that exact purpose. As a matter of fact, the Debian deal it is just an excuse - a literary device, if you will - to explain how and why I decided to have a crack at it, because I had my hunches true to what I called it – this pendrive is EVIL.
The flash drive is of unknown make and model, it's generic-looking, it's just a clone of a GoodRAM Twister drive, the likes of many you’ve probably seen a million times before. There seem to be a few models that the manufacturers have taken quite a liking to, and most of the cheap stuff is the same few models cloned to exhaustion. This is one of them.

(The 64GB pendrive compared to my 16GB GoodRAM Twister. The Twister is well used and as such the engraving on the swivel part is barely visible anymore.)
Frankly, from the outside the pendrive is rather unremarkable and there’s not much to write home about. It makes for an absolutely stellar fidget toy if you’re a restless young gun like me. I’m playing with it right now as I write this article, actually. The only thing of note is the “64GB” sticker, the style of which is common for products that also have a “QC” sticker slapped on haphazardly, if you catch my drift. And it is quite telling of the nature of this flash drive. You see, as likely you have already guessed, it probably isn’t 64 gigs in size, nor even the half of it.


(Above: GoodRAM Twister 16GB. Below: Pandora’s Box)
If we take the shell off – it’s not glued in any way, just plastic posts and holes – we see a pretty standard flash drive PCB. Despite being the same thickness as the GoodRAM one, it looks a bit shorter and, well, cheaper. Interestingly, the USB port displays some signs of patina and usage, even though I have barely opened the package. Could it contain used parts inside?
We see more clues once we take a look at the chips inside. You don’t need much in order to have a working pendrive – some sort of flash storage IC, a USB flash controller (it has all the glue logic to be able to communicate with the PC or other device through the USB protocol), pepper it with some passive elements so that the current is filtered, yadda yadda yadda. Here they are:
Again, both are unremarkable – only that the 64GB flash drive’s flash memory IC is notoriously hard to find any proper info about. I scoured Google and all I got were loads of merchant links, stock breakdowns… I legit could not find a single datasheet! What’s more, some links claim that this chip was made by Toshiba, but this cannot be confirmed in any way. The date code indicates the 26th week of 2008, which may yield to the idea of used or refurbed chips. Plus, if you think about it, it would have been state-of-the-art for 2008 if it had 64 gigs of space, wouldn't it?
Okay, it’s fake. The big reveal, right? It’s not as if one could expect it from the way the text unravels; mind you, however, that this fact would not have likely merited a writeup if it was a bog-standard fake flash drive. And it’s anything but – not in one factor, but also another, much spicier one.
If you think about it, manufacturing and selling fake flash drives (or any flash media such as an SD card or SSD for that matter) is a perfect crime. First off, the customer might not notice anything being wrong until it’s too late – we’re talking about storage that claims to be, say, 256 gigs but is only 128 – that way one can assume that it’s not going to be filled up quickly enough to notice it within return, warranty or other claim policies. Second, the seller can simply state the storage is defective, misdescribed, or that the customer didn’t read the fine print. Really, anything could be an excuse, and worse still, the seller can just vanish into thin air. Third, not everyone is going to go the lengths of disassembling the thing to check or prove it being fake even for the fear of such banal things like lack of skill, unwillingness to tamper with media that could have some data on it already (especially if it’s precious) or… voiding warranty. The last argument is contestable, and we should be thankful for the kind people who developed software that specifically tackles the issue of checking if the flash storage you just bought could be a sham.
There are two main ways fake USB sticks work. Both involve misreporting the real size to other devices, practically always stating that the storage space is bigger than it really is (it wouldn’t make much sense the other way, would it?). This is done by programming the flash controller, i.e. the “brain” of the storage media that communicates with other devices and manages reading and writing data – it’s easy to do, given you have the necessary hardware and it could be a batch job that would be then spread over flash memory ICs of any size. The trick lies in managing this data that would be written to a fake pendrive. How are you going to cram files whose size goes beyond the drive’s physical space? You don’t! You either a) send all data beyond the physical limit to be written into nonexistent space that is nonetheless “seen” by the device sending data, effectively sending it to null, or b) send the data beyond the physical limit back to the beginning of the flash storage space, sector 1 or what have you, and loop over the data that was already copied and stored before, over and over and over again. Those two beautiful lies are clever and nefarious at the same time.
I should mention another method of scamming buyers on their flash storage, though this is pertinent to SSDs and SD cards more than flash drives: the capacity may be as indicated, but the performance may be so God-awful that it’ll make you wanna defenestrate the thing. There’s also thermal hijinks, cache (rather the lack thereof) hijinks, or downright abominations that house SD cards and a USB 2.0 controller in a NVME.
I wanted to sound hopeful in this bit, but sadly, users are vastly underexposed to essential knowledge about these scams in my opinion - especially the less tech-savvy average buyers. This stuff is rampant to the extent of appearing in retail stores and respectable online platforms; you may have heard of Amazon selling fake SSDs – even Linus Tech Tips shone light on the issue. Maybe I’m getting ahead of myself, but it’s not even the matter of flash store being “counterfeit”, as Internet sources seem to use the term interchangeably with “fake” or “scam”. One could buy a Samsung that reports its size fine, but, let’s say, the barcodes/holographic stickers are off. Fake. One could buy an SD card which states it's 128 gigabytes, but is only 64. Also fake. Many seem to point prospective buyers to being wary of only the brand symptoms, and the rest of the market gets left out. There are a lot of smaller brands, badge-engineered marques, store brands and no-names that sell lots of flash drives, and they all could be affected with the fake storage space trick. A frugal PC enthusiast could buy a positively-reviewed SSD from Temu or wherever everyone gets their hyperconsumptionist high off nowadays; a non-tech-savvy aunt buys USB sticks to fill with family pics for the family; both get smoke’n’mirrored. You get the point - I feel like there’s two levels to the problem of porking people on storage media and they’re not both given adequate attention.
Now that we’ve got the explanation out of the way, we’re going to see how we can catch a fake flash drive faking itself. I’m using FAKEFLASHTEST – a nifty tool that seems to be made by the same person who also made Easy2Boot and RMPrepUSB, two fine utilities that I am a happy (albeit occasional) user of. Hats off to you, kudos!
The program has two main tests: “Quick Size Test” (Destructive), which I’m not sure what it does, but the drive needs to be reformatted afterwards; and “Test Empty Space” (Slow), which fills the drive with files until it stops at its limit.
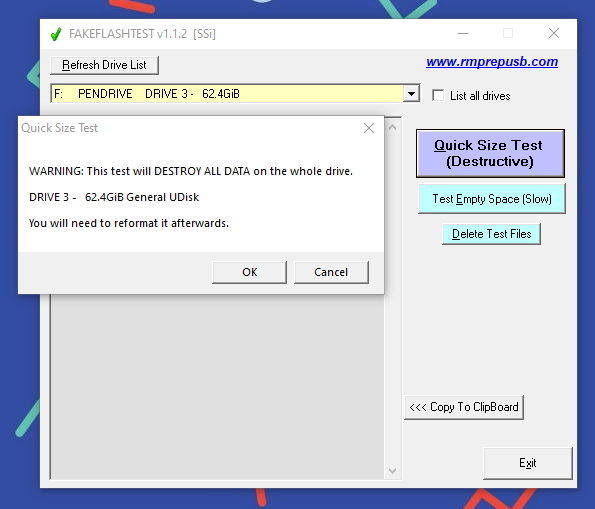
(The pendrive visible in FAKEFLASHTEST, in all its 62.4 gigabytes of glory)
I selected the pendrive in question and chose “Quick Size Test” (Destructive) – honestly I didn’t even bother with the second option, because after literally 3 seconds I already got the answer:
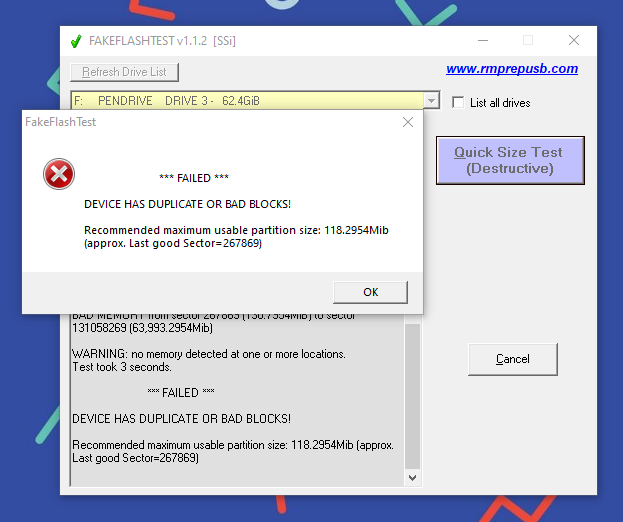
(Talk about overcompensating for your size)
It’s so horrible, it’s funny. 118 megabytes! That’s only over 512 times less than indicated! (I gather it’s really a 128MB IC.) It exceeded my already low expectations to the point where I’m at a loss for words – I had expected a gigabyte, or something in the same, reasonable ballpark! Imagine being such an ass that you produce USB sticks with such size. There’s something inherently ridiculous and funny about 128 megabytes of storage space, not more, not less in the contemporary context. Like, I don’t even know what to do with the thing! Had it been a gigabyte or two, I could have found some use for it, but this? What am I gonna do, plug it to a 486? Act as a RAM disk for something? Stick it into soil and hope more bytes will grow?
Atrocious size aside, this shows how simply you can check your flash storage if you suspect that it might be sus – no disassembly, no voiding warranty, nothing – in that case, you could have just returned it to the seller, no extra info provided and no questions asked. That is, of course, if you didn’t win it and a few years didn’t pass since you got it.
Oh yeah - for Linux, you can use a tool called f3 (Fight Flash Fraud, rolls off the tongue) and check if the usable size of the drive is equal to its announced size. If it differs, it’s fake.
There are three things I’m curious about, now that the mystery is solved:
The cost is probably miniscule, and with big enough orders on the wholesale tip I guess that all those cheap fake flash drives are making a killing for the sellers. The second question is a moot point as I’d have to find it out in some way, most likely empirically by buying a bunch and cracking them open, and the answer to the third question is a resounding: yes! (kinda)
It’d be neat to be able to use it without it nuking files after the 128 MB limit, even if just for kicks. This can be done using diskpart – use the command clean, then create a partition the size that was reported by FAKEFLASHTEST - create partition primary size=118 in my case. That should work, for whatever it’s worth. Also, when I tried doing a standard format over the Windows GUI tool, it hanged immediately at 0%, lol. It never moved in over an hour!
That’s pretty much it for the fake size aspect of this pendrive. Hang on, though! I’ve intentionally skipped one thing that would have kind of undershot the effect had it been revealed earlier. When I plugged the USB stick in for the first time, I should be lucky that I did it on a PC that I do not actively use.
Reason being, the fake flash drive holds a little present ;)
"...It’s our way of saying thank you. Keep your free gift."
Alright, when I first plugged this pendrive into a PC – a Dell Optiplex 755 that just sits around most of the time doing nothing, running Windows 7 – I immediately got an alert from Windows Defender about a virus. If you’re surprised about Windows Defender and Windows 7 being used in the same sentence, I was indeed surprised as it was turned on on that Win7 install! The PC belonged to my family and the OS installation is very old, but rather clean.
Anyway, yes, it rang the alarm bells, Windows Defender woke up from its slumber and pointed to a location on a drive letter belonging to the flash drive. Which was strange, given that it was, uh, brand new? The pendrive contained a hidden package, tightly wrapped as follows:
E:\RECYCLER\S-1-3-01-8626833318-5550716012-354253382-5002\HXvsaqkP.exe
While it seems to be an irrelevant path, it clearly imitates a Windows system folder which stores the items placed in the Recycle Bin on the desktop. Interestingly, at first glance I thought this was a misfortune on the side of the threat actor as I only recalled there being a \$RECYCLE.BIN\ folder for that in Windows, so I was like, “ha! dweeb!,” but as it turns out, \$RECYCLE.BIN\ only was used since Windows 7, and \RECYCLER\ was implemented in early NTFS-centric OSes like XP and Vista. The more you know, huh. The string of numbers starting with the letter S is the SID – Security Identifier – a signature of sorts of the user who deleted the given file – and the random file name imitates a file sent to the recycle bin. There’s an amazing blog post about recycle bin forensics that I highly recommend if that bit got you interested.
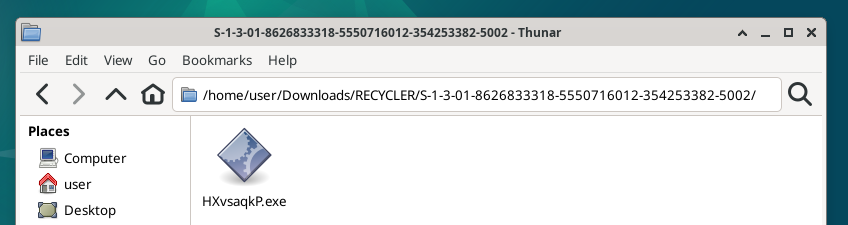
(The malware path seen in Debian. Ignore the “Downloads” part of the path, please.)
(For comparison – a standard Win10 recycle bin with some recycled files.)
The whole thing had hidden attributes, like the regular Windows trash can, but clearly it had “evil” written all over it. I can hardly believe a recycle bin folder on a factory-fresh drive. I got curious, so I promptly swiped it off from quarantine and zipped it so it was safe for further research at a later time. Hence the disruption between plugging the drive and checking whether it is fake.
When I got round to it, however, somehow I missed one particularly nasty aspect about this “virus”, namely that the fraudulent “recycle bin” folder contains an autorun.ini file as well! The autorun file contains 5 pages of random text and a autoplay function for the malware file sandwiched between the gibberish. That way, it runs the moment the flash drive is plugged into the computer, which can catch an unsuspecting user completely off guard; for that matter, the more tech-savvy or security-oriented folk might get got as well, as a police department in Taiwan showcased back in 2018. Some headlines really write themselves, man.
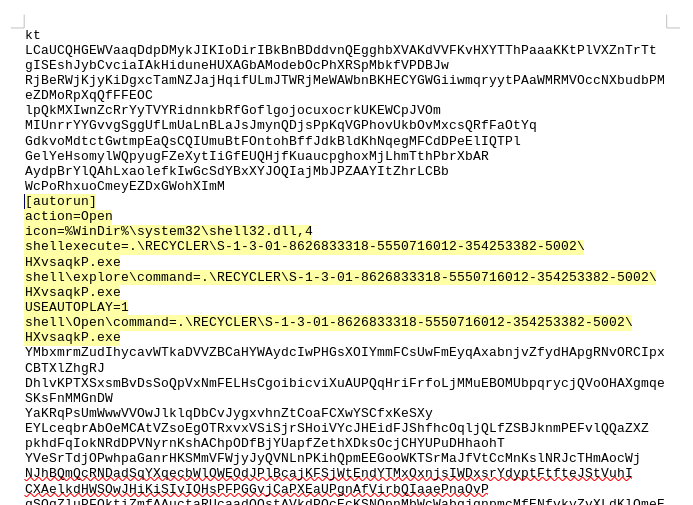
(2 points for style, 10 for ingenuity)
Admittedly, we gotta give props to the attack vector of choice. The autorun and autoplay functions seem to have faded from user consciousness in recent years, and that’s not hard to believe – after all, disc media – the last stronghold of the olden days, which liberally used autorun, especially third-party media that the user didn’t burn themselves – is but a song of the past. I don’t think I need to provide arguments for this standpoint now that neither desktop PC cases nor laptops have any physical cutouts or provisions for optical media anymore. Of course, you still use CDs, and so do I honestly ;) – but the average Joe? Hardly so. With the advent of pendrives, the idea of transferring files has also changed in a way, I guess? By that, I mean that you don’t usually get drivers or software from a vendor on a USB stick, but download them from their website; meanwhile, pendrives themselves are the epitome of sneakernet – copy a few files, go somewhere, drop these files, and do it again at some later point, all the while the good old autoplay function remained across subsequent Windows releases. It’s like a 1-2 sneak attack because I admit, and so should you, that autoplaying something from the pendrive likely isn’t the first thing that comes to your mind when using such media.
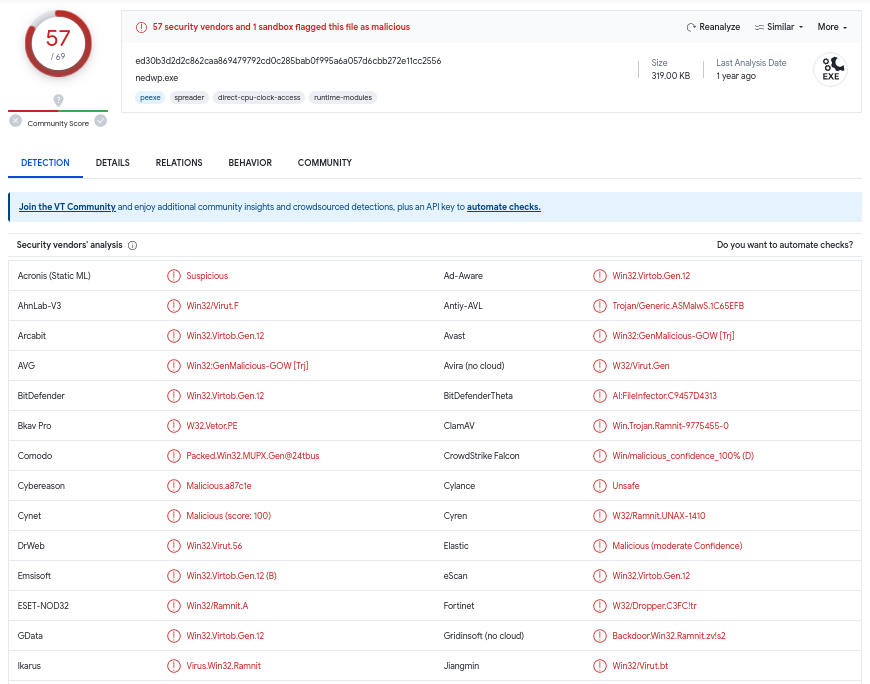
Let’s take a look at the malware itself now. It’s an interesting one – a VirusTotal scan of the file lists it to be a variant of Virut (alias Virtob), a once-incredibly prevalent piece of ugly. I’m no cybersecurity expert and I will spare you the details, but simply put, Virut is a very sneaky, shapeshifting program that confines your PC to a botnet, back when botnets were used for spam, DDoSing, sideloading adware and spyware. If you want to learn more about Virut check out this fantastic writeup from the masters at work.

(The VirusTotal result of HXvsaqkP.exe)
It had its heyday from somewhere between 2006 to 2013, when a sinkhole operation was commenced and the server domains hosting the botnet were taken over by the good guys from a Polish R&D lab and the operator of the .pl domain registry, NASK, which dealt quite a blow to the malware operators as they lost control of many infected computers which communicated with the retaken servers. Which… seems a bit odd of a choice for sneaking into a flash drive in late 2010s, considering that the crippled botnet was probably on its last legs or inactive, not to mention that antivirus vendors probably had their virus signatures polished and sharpened for every iteration and manifestation of a decade-old virus that was Virut. It just feels like a wasted opportunity.
Wanna hear a conspiracy theory? When reading about fake pendrives and Virut some information found online exhibited some… connections, let’s say. There’s this article on Malwarebytes’s blog, dated March 2018, where the almighty Hasherezade notes that… a then-recent drive-by-download campaign (unintended download of software, typically malware, through a Web browser) stemming from China carried our friend Virut as a hitchhiker along with the main payload. I tried to dig deep into my memories and can place the event of obtaining the fake flash drive in the early spring of 2018. – roughly the same date, and same payload. And if we dig into the Taiwanese cop giveaway slip-up, even more clues arise – the pendrives were infected with a random-named .exe file, there's a mention of a server in Poland, same as Virut’s servers, and that the malware stole personal data… like Virut! Could these events be connected? Could it be that some threat actor was in cahoots with a supplier through some shady dealings and was staging a reboot of the Virut botnet? Hmmmmmm…
Many of the things mentioned in the whole Taiwanese pendrive deal don’t really check out on a rational, connect-the-dots basis, and it kind of undermines this whole theory’s interconnection. The article mentions a crime ring being shut down in 2015, whereas Virut was sinkholed in 2013; in addition, whereas The Register’s article states an “operating system” of some sort being put on the flash drives (what, Kali Linux? What OS could they have installed for an infosec quiz, and more so – why?), its original source (here, in Chinese) contains no mention of any OS being installed at all, just some “testing”, and tells a story about how a worker “copied” the malware onto the drives. Plus, much to my dismay, I couldn’t find any concrete information about how exactly it spreads through flash drives – most information found online is pretty bare, I found only mentions of spreading through executables. But HEAR ME OUT!! In that case, how did the host file end up in a deleted folder if the pendrive was brand freakin’ new? I have no idea what the infected host file is exactly and the only logical assumption is that the file is somehow involved in pendrive formatting (or, in the case of my USB stick, something regarding screwing people on reported flash size). And even this assumption still does not explain the file being in the damn recycle folder of a new flash drive!
It would be your best interest if you disregarded the above two paragraphs as all this is far-fetched.
…unless? ;D
There’s a couple of takeaways we can gather from looking at this unholy fidget spinner, and the one I’m going to start with is the most important: Be careful! Be careful of flash storage bought online, especially from retailers you have doubts about. There’s a slew of no-name pendrives, many of which come in the same shell and swivel as my fake stick, which can be had for like $3 for 64/128GB and the listings I found have hundreds and thousands of orders. A quick search for a similar-size flash drive from a reputable brand (SanDisk, Kingston, GoodRAM) shows they go for roughly 3x the price of no-names, sometimes more. And I’d recommend sticking with those reputable brands – do your research, do your due diligence, however cursory it might be. Read reviews before you take a risk on something that’s cheap, noname, or rises any doubts. We’re talking about your data at stake, which can be threatened by the fake loop-the-loop size or whatever devil that lies within those flash drives and flash storage in general (and we all know damn well that people as a rule don’t do backups). Caveat emptor.
Be careful of what you stick into your computer. Yes, I know, sometimes it’s just not possible – you only have one PC and you need to do copy something fast, and you don’t have time to download and install an antivirus, and the flash drive comes from a friend that you know half your life, and… the bare minimum you could do is try enabling Microsoft Defender for a few minutes. It’d be a good idea to also disable autoplay on your PC – I would argue that you’re not going to need it in this current era of computing.
Next, a couple of words on the context of the pendrive falling into the hands of yours truly. You would think that whoever had a hand in organizing the contest which, mind you, was IT/English themed and took place in an IT-leaning technical school, would have noticed anything with the pendrive. It’s such a cruel twist of irony. “They might have had not that big a budget. What do you expect?!,” I hear in response, as fists are shaken in the air. Okay. Buy a brand-name 8GB drive instead. I would’ve been fine with it, and 8 gigs are infinitely better than sorceringi 128 megs with a virus as an extra side. On that note, what’s less funny is the prospect of somebody else using the fake flash drive. Say, for instance, that my mom or my brother, or the aforementioned aunt character, one sunny day stumbled upon the flash drive in the drawer before I did, thought that they could use it, and absent-mindedly plugged it into their computer - which happens to be the site of their work, banking, social networking, or passwords and sensitive data stored in a plaintext .txt file. Or that the aforementioned aunt character decided to move all their holiday photos to such a flash drive, which would be sent to oblivion without her knowing – until she wanted to plug the pendrive to a TV on a birthday party, as people tend to do. This is the most worrying thing I draw from this writeup – that this stuff is real and out there in the wild.
Lastly, old malware never dies, it seems. We’ve already seen some old school viruses that despite the quantum leap that computers have achieved in the last 3 decades can still be found in the wild. And while many may seem harmless now due to powerful virus signature databases or simple compatibility problems, we must remember that a virus is not just this romantic imagining of something that will display cool images on the screen and nuke your MBR, but rather it’s a game of credentials, personal info, spying, and access without consent. We’ve seen here that even Virut could potentially still wreak havoc; so, who knows when some ancient monster (preferably of x64 architecture) rears its head again?
If you’re keen to learn more about Virut I’d like to share some sources that I found interesting. One is an article from late 2018 (note the date) by Prof. Dr. Christian J. Dietrich, who muses on the events that have happened concerning Virut in that year. Worth a read. NASK, the entity responsible for taking over the domains used by the botnet have published a report on the operation. The English-language version is a 404 error on NASK’s website but some kind soul archived it on Github. For those in the rabbit hole, there’s a neat article about malware archaeology, as well as a DEFCON talk about the history and evolution of computer viruses. As for old malware coming back, this blog post by Mandiant describes that even in 2021 Virut still pops up from time to time, along with throwback names such as Sality, Ramnit, and Neshta – which alone deserves a separate article.
A quick thought: perhaps opening the host file that was present on my flash drive could give us any indication if indeed flash drives were tested using some sort of special software. You know, if it turns out to be some formatting tool – or a completely unrelated file which would point in the other assumption - then maybe it would provide us with some sort of a conclusion to whether it was a mistake, a joke, or an orchestrated attack preparation >:) Maybe some other time.